Current solution - database of viruses
Current solution - database of viruses
Antivirus works with a database of viruses. What is not in the database may not be recognized. That was the problem the virus Stuxnet, DarkHotel, Regin and many, many others. This is a huge issue of current solutions.
The Three Laws of ICT Security - database of checksum of files
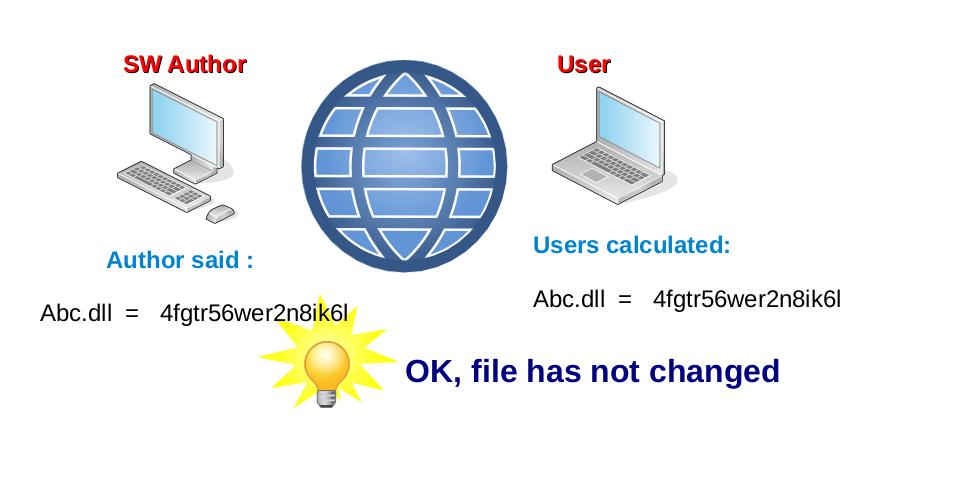
Author SW entered information of system files (* .exe, * .dll, etc.) into a database of checksum. User or security module in the device verifies the checksum / file integrity. Virus or hacker have limited space. Any change in the file changes the checksum of file on the user's device.
Virus or hacker can not modify a system file.
Checksums of file which published author SW = Checksums of file on the user's device.
This is a change in approach. The shift from the search for already known viruses to the solution which verifies the originality of origin (integrity).
The approach is very similar to the verification of original spare parts for aircraft.
What is not on the database (in the new service of Internet) is considered suspicious.