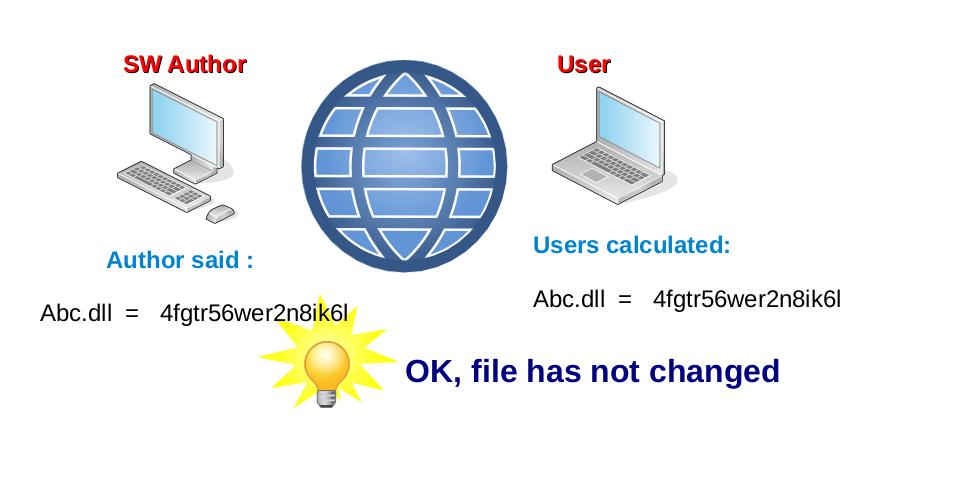
1, Basic level - Integrity
The Three Laws of ICT Security ensures (guard) the integrity of the operating system, programs, and system libraries. Computer viruses and hackers then have a very, very limited space for the attacks.
 ICT space with the Three Laws of ICT Security :
ICT space with the Three Laws of ICT Security :
Viruses do not have a chance to hide in the PC, mobile, SCADA, IoT, etc. Is not a chance run viruses in PC, cell phone, SCADA, IoT, etc.
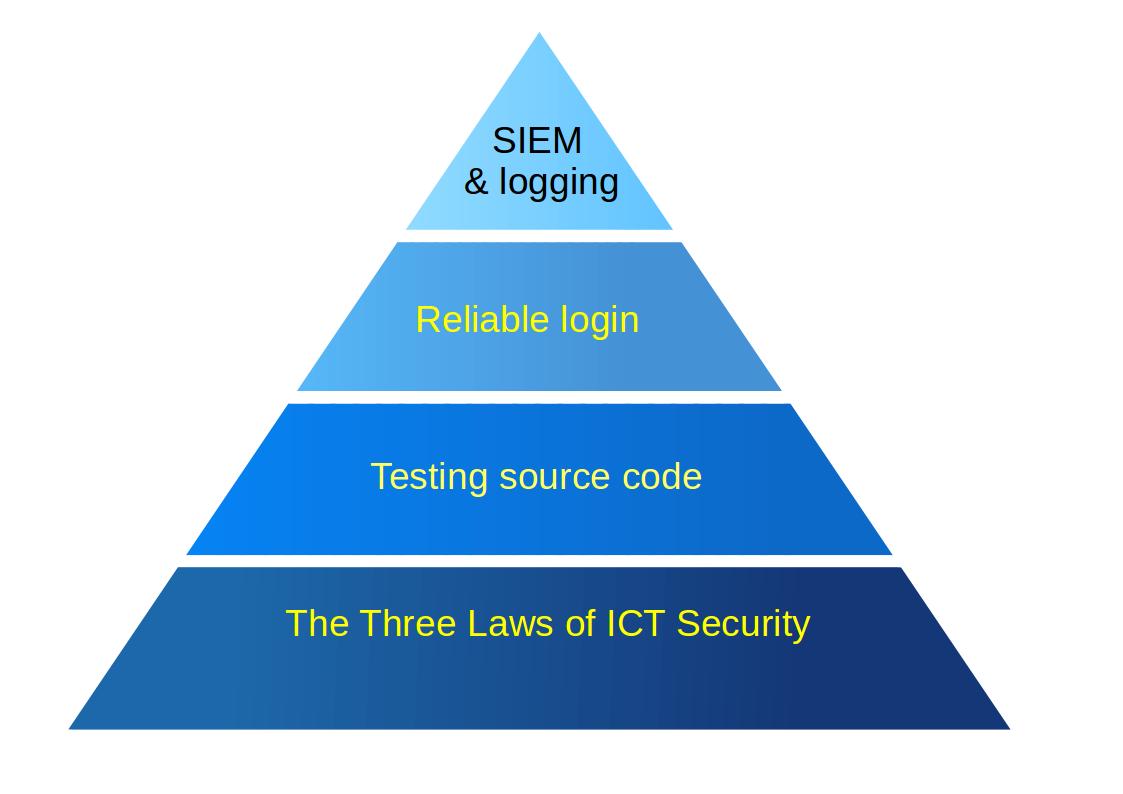
2, Second level - Testing source code
Software development is an exact discipline. In the area of development and testing of software, it is necessary to describe the procedures and functions clearly. In an environment based on a clear description of the tasks can be implemented a clear control.
ICT space with the Three Laws of ICT Security and Testing Source Code :
Testing source code limits the scope for exploits and for one-off attacks. One-off attacks are guarded and blocked at basic level
3, Third level - Reliable login
Login into the System has reliable basics. In first level is checks the integrity of the files, in second level are tested source code. Keylogger has not a chance! In this space, it is possible to explain to users the importance of login password.
4, Fourth level - Logging